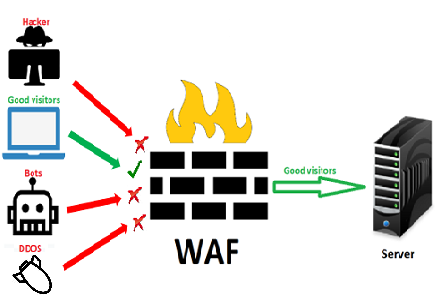
We have implemented WAF (Web Application Firewall) protection system on all our hosting servers. The system along with the security rules are used by our administrators.
What is WAF?
WAF is a system for protecting web applications. Thanks to it, we can control the movements to our application and from it without any user intervention. The whole procedure happens automatically after the administrator sets the rules for filtering such traffic.
The WAF system has been equipped with a set of rule rules based on the OWASP (Open Web Application Security Project) program, which are constantly updated.
The main mechanisms of the system operation, limitations prevent:
- access to the server, we rely on the reputation of IP addresses
- DoS attack (Denial of Service)
- Attack. Separation of HTTP responses, LFI (local file attaching), RFI (local file attaching), XSS (scripts between sites), SQL injection, session repair,
- data leakage from both SQL, JAVA, PHP and other data leaks
Can I disable the module on my blocked hosting?
By default, all hosting accounts have the WAF system available. Users on their access to hosting in cPanel have the option of using this system. This is not recommended because it can cause attacks on websites, which in turn may cause the website to stop working, for example.
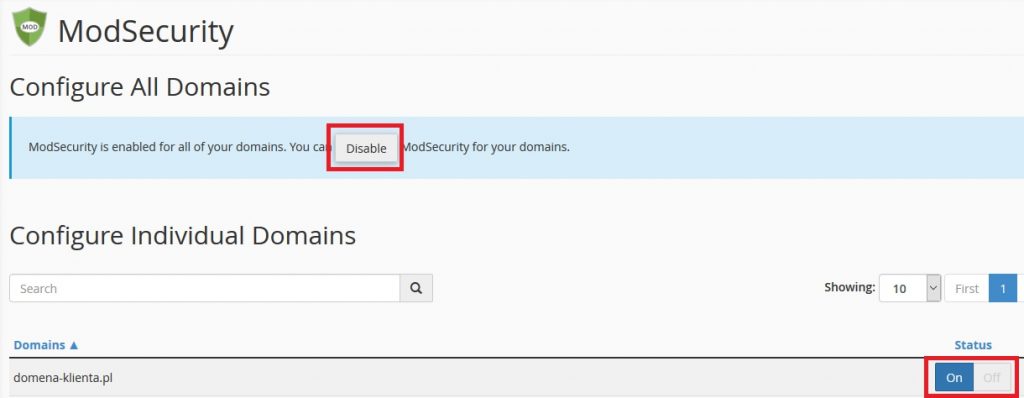
To include (not recommended) go to cPanel and then look for the “ModSecurity” option in the “SECURITY” section.

The system can be turned off completely for the hosting account by clicking on the “Disable” button. We will be warned then that our domains will lose additional protection provided by this module. Then click “Disable All” and the module will be disabled for the entire account.
The second option is only separately for each domain / subdomain. In this case, press the “Off” button next to the selected domain. If you need to disable protection for a particular site for some reason, it is advisable to do so for individual pages, not for the entire hosting account.
If you notice any problems in the operation of any of the options, please contact us at hosting@smarthost.eu
WAF system statistics
Is WAF needed? For example, we can state that on one of our servers (representative, with the same number of clients as most of our servers) in the last 5 days were blocked … 138,452 attacks.
Examples of attacks that were blocked (they all came from the outside, most often they were attempts to call a website with additional, properly crafted parameters that were to harm the website):
- Path Traversal attack – is carried out on applications that allow uncontrolled access to files and directories that the user should not normally have access to.
- XSS Injection – false XSS injections in nested url
- SQL Injection – SQL injections or the use of a vulnerability in the network that allow an attacker to interfere with queries sent by the application to the database.
- PHP Injection – is an application-level vulnerability that, depending on the context, could allow an attacker to perform various types of malicious attacks, such as code injection, path repetition, and denial of service.
Currently on all our servers attacks of similar types are intercepted on the fly and neutralized by WAF.
- A direct connection between Smarthost and Cloudflare - October 2, 2024
- Why is Redis better than Memcached? - September 16, 2024
- What is DMARC and why should you have it? - July 12, 2023